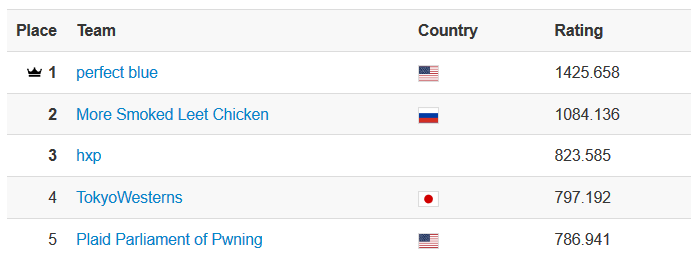
perfect blue finishes #1 on CTFtime 2020
perfect blue finished at the top of CTFTime rankings for 2020 season with 1425 points. 🏆
Overall, we won 🥇 1st in 12 events, 🥈 2nd in 6 events, and 🥉 3rd in 5 events out of the 36 events we participated in.
If you have arrived to this page without any context, feel free to refer to the section What are CTFs.
Introduction
First, we’ll briefly cover how perfect blue formed and our CTF journey up to now. We first met at CSAW High School Forensics in 2017 and started with just 5 members: Jazzy, VoidMercy, cts, neptunia, and slenderestman. We played under a different team name then.

For 2018’s DEF CON CTF quals, we added two members: Sampriti and Jonathan Jacobi. That’s also when we took on our name, perfect blue, and created our logo.

Though we didn’t qualify for that DEF CON, we took that team to our first major on-site at WhiteHat Grand Prix in Vietnam.

Our first big win finally came in 2019 when we placed #1 in CSAW quals and finals.
Over the last two years, our team grew from 5 to 14 members. Most of our members are located in the 🇺🇸 U.S., but we also have members from 🇨🇦 Canada, 🇪🇪 Estonia, 🇮🇱 Israel, 🇰🇷 South Korea, 🇳🇴 Norway and 🇦🇺 Australia.
- Jazzy
- VoidMercy
- cts
- neptunia
- sampriti
- jonathanj
- theKidOfArcrania
- braindead
- knapstack
- typeconfuser
- corb3nik
- rbtree
- vakzz
- UnblvR
We’re a tight-knit group of friends who play together. The main motivation for us has always been free travel to have fun at onsite events. Most of our members are college students along with some professionals who are well-known in the infosec community.
perfect blue finished 9th place on CTFTime in 2019 and 1st place in 2020.
Fun Facts:
- We love anime
- We use 様 honorific when we refer to braindead, because he randomly pops into a channel and posts ‘solved’ with the flag
- The pb logo is a golden spiral
- Our favorite animal is the 🐍 snake and our favorite food is 🧀 cheese
2020 Season Overview
It’s been a great year. Cheers to all of our teammates, our guest members ptr-yudai, aventador, st98, hgarrereyn, muld0r, defund, and noopnoop, and our collab team Super Guesser. This wouldn’t have been possible without everyone’s hard work and dedication. During 2020, we solved challenging, creative tasks, made new friends, and organized our own CTF, pbctf.
CTF during the pandemic
COVID affected nearly all aspects of life, CTFs included. Being stuck inside sucks, so we ended up playing a LOT of CTF. This is what our schedule looked like for the last 3 months of 2020:
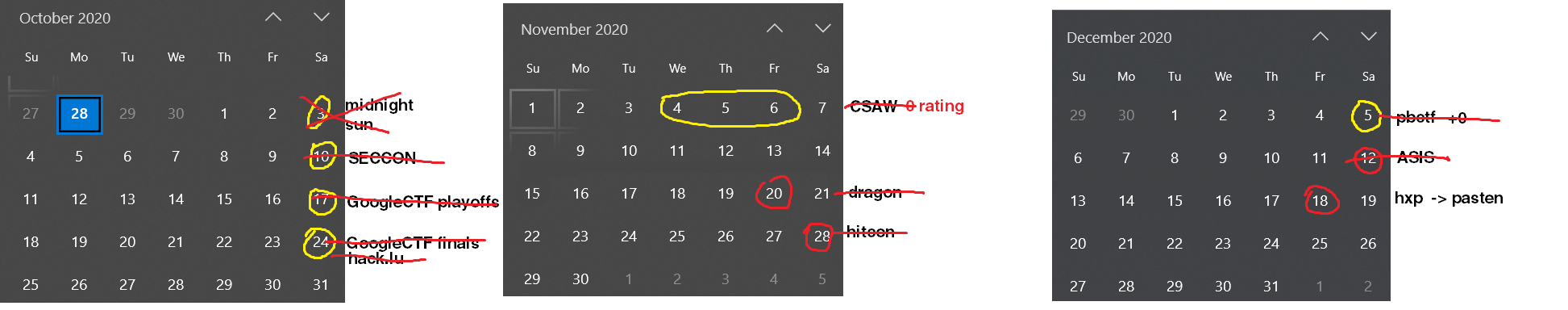
As you can tell, we were grinding pretty much every weekend. Regrettably, despite the stellar performance, COVID cancelled all the free travel 😔

Timeline of 2020
January–March
In January, we started the season on a high note by winning WhiteHat Grandprix quals 🇻🇳, the first CTF of the decade.
In February, we traveled to San Francisco to participate in BSides SF CTF 🇺🇸. Although we won, sadly that was the only CTF we would attend in-person all year.

April–May: A turning point
April picked up the pace with two top-tier CTFs in a row. These premiere events are known for their punishing challenges, great quality, high rating(?), and fierce competition from teams around the world.
First came PlaidCTF 🇺🇸, organized by the Plaid Parliament of Pwning (PPP) from Carnegie Mellon University. PPP has a long tradition of being one of the best CTF teams in the world (they’ve won 3 CTFtime seasons since 2011). Unsurprisingly, PlaidCTF is also one of the top events on CTFTime. Despite our efforts, we finished 10th in PlaidCTF.
Our next stop was DEF CON CTF Quals 🇺🇸 in May. It’s arguably the most famous CTF. With history spanning back decades, DEF CON CTF is also informally known as the “olympics” of the CTF circuit. Though qualifying for finals has always been on our bucket list, perfect blue seems to have a curse, falling just short each year: by 1 spot in 2018, 1 spot in 2019 as OpenBlue (a collab with OpenToAll), and once again in 2020.
The disappointing results from these two competitions forced us to rethink our approach towards top-tier events. Many top teams are the product of repeated mergers and acquisitions. For example, MSLC = Leet More + Smoked Chicken, Organizers = cr0wn + Secret Club + emwtf. Teams also often informally congolmerate into “super teams” for major events with fierce competition. Oftentimes, these teams form based on nationality. This is especially true for DEF CON quals. This year, /bin/tw 🇯🇵 = Binja + TokyoWesterns, More Bush Smoked Whackers 🇷🇺 = MSLC + Bushwhackers, and HITCON⚔Balsn 🇹🇼 = HITCON + Balsn. Other superteams included mhackeroni 🇮🇹, NorseCode 🇸🇪, Sauercloud 🇩🇪, and koreanbadass 🇰🇷, which were Italian, Swedish/norwegian, German, and Korean respectively.
Comparatively, perfect blue is relatively small. This eliminates the margin of error during CTFs, and anyone getting stuck on a task could derail the competition. Outside of competitions, it also means carefully juggling real-life responsibilities with CTF and arranging your activities and sleep schedule around major events. Being #2 on CTFTime around May and neck-and-neck with other teams, we saw this as a challenge: to finish #1 in 2020. That motivated us to make a stronger comeback for the rest of the season. We forged ahead and kept our spirits high for the second half of the year.
June–September: Intermission
The summer marked a lull in the CTF season, without too many major competitions.
Around June, we participated in a fancy space hacking contest, Hack-A-Sat 🇺🇸. This was a new refreshing experience. We learned a lot about space hacking despite not qualifying for finals. We also published a blog post writeup for a challenge we particularly enjoyed.
We were also invited to the 3rd International Cyber Mimic Defense Competition 🇨🇳 organized by cyberpeace. It’s normally held in Nanjing, China, but unfortunately, it was online-only this year. We finished 1st in the International teams category.

At the end of June, we participated in another top-tier event, 0CTF/TCTF Quals 🇨🇳 organized by Tencent, eee, and the mighty chinese powerhouse 0ops. After a long battle, we finished 3rd and qualified for finals. Nevertheless, we were bested by koreanbadass & MSLC who finished 1st and 2nd. The challenge quality was great and featured a Chrome pwnable series (our writeup here).
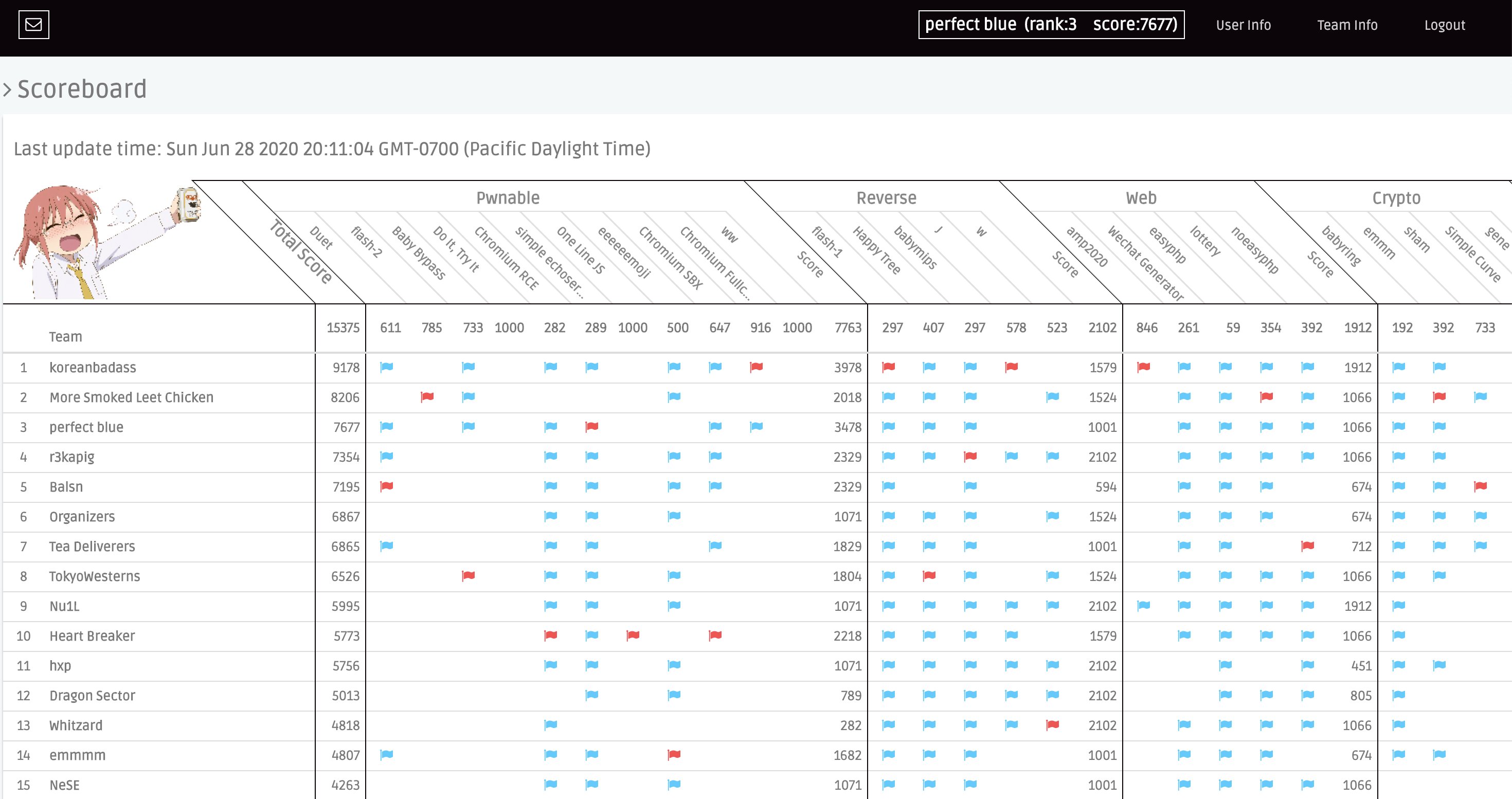
In August, we played in Google CTF 2020. We finished at 7th place globally, qualifying for Hackceler8. Hackceler8 was an experimental live-streamed “live hacking” competition where finalist teams showed off exploits for a browser game. We were excited to be part of it. Unfortunately, the official competition video still hasn’t been published yet at the time of writing :-)
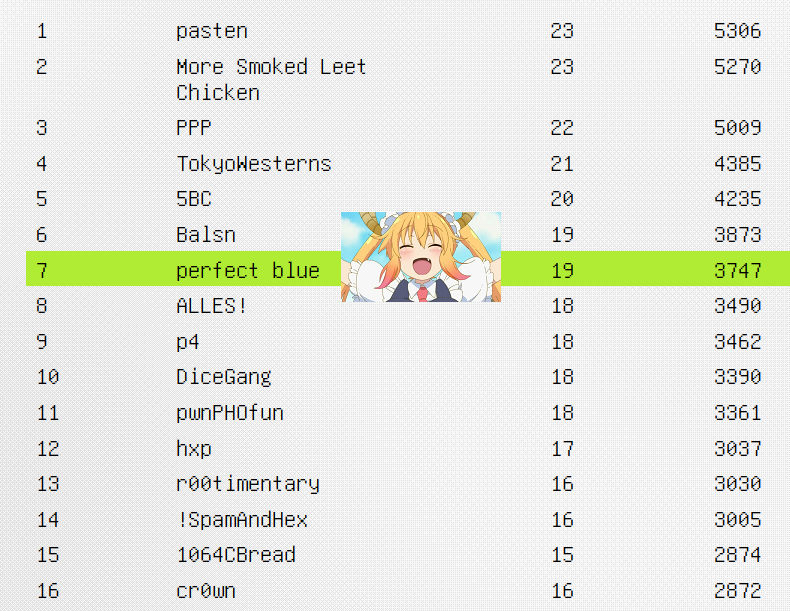
In September, we qualified for CSAW Finals, and we also played in TokyoWesterns CTF 🇯🇵. We finished in 2nd place for a cool 144 CTFTime points.
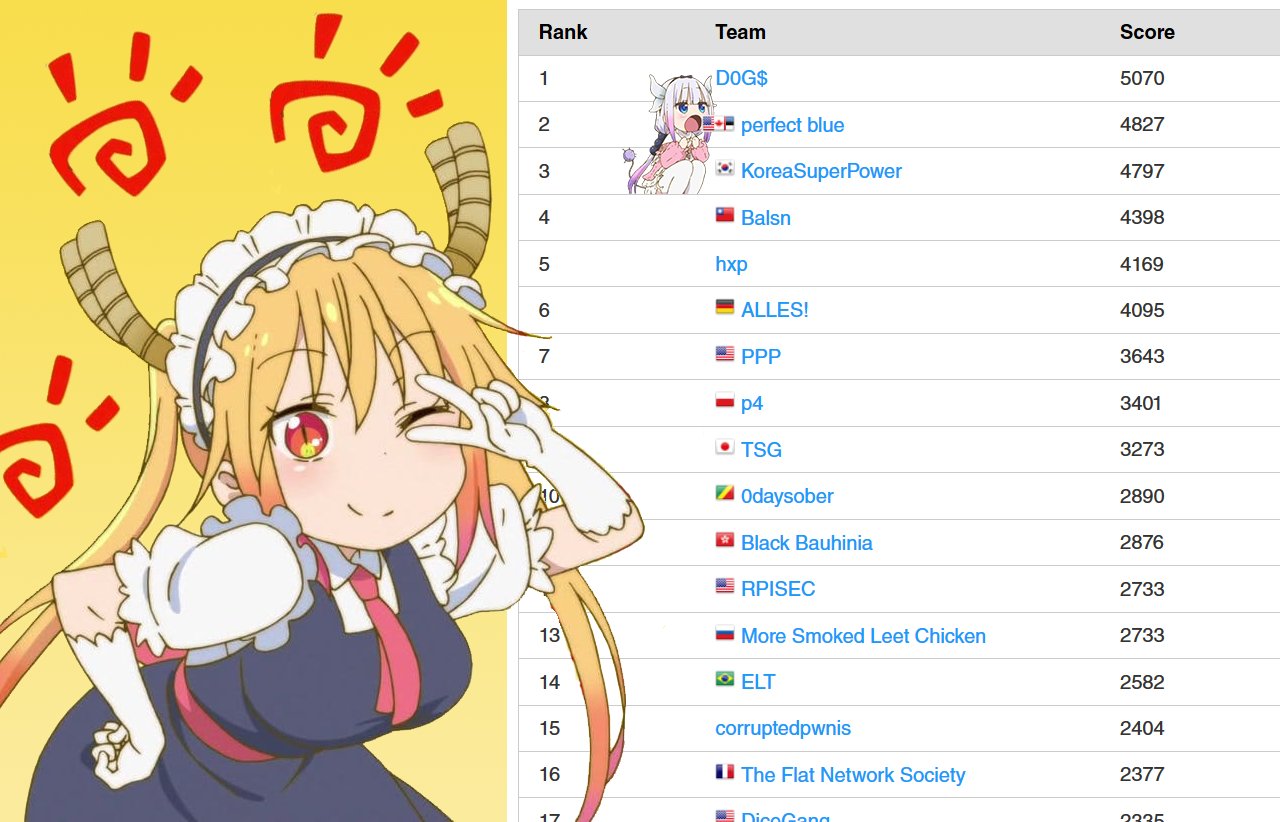
October–December: Sprint to the finish
October marked the finale of the season, with top CTFs nearly every weekend. In preparation, we took a well-deserved few weeks of rest after TWCTF so we could grind out the last 3 months without risking burnout.

From that point onwards, however, we went full throttle. We finished 2nd in SECCON Quals 🇯🇵 on Oct. 10, participated in Hackceler8 on Oct. 17, and on Oct. 24 we won HackLu CTF 🇱🇺 organized by FluxFingers (with a great pwnhub theme). We secured 261 CTFTime points in total from these 3 events.
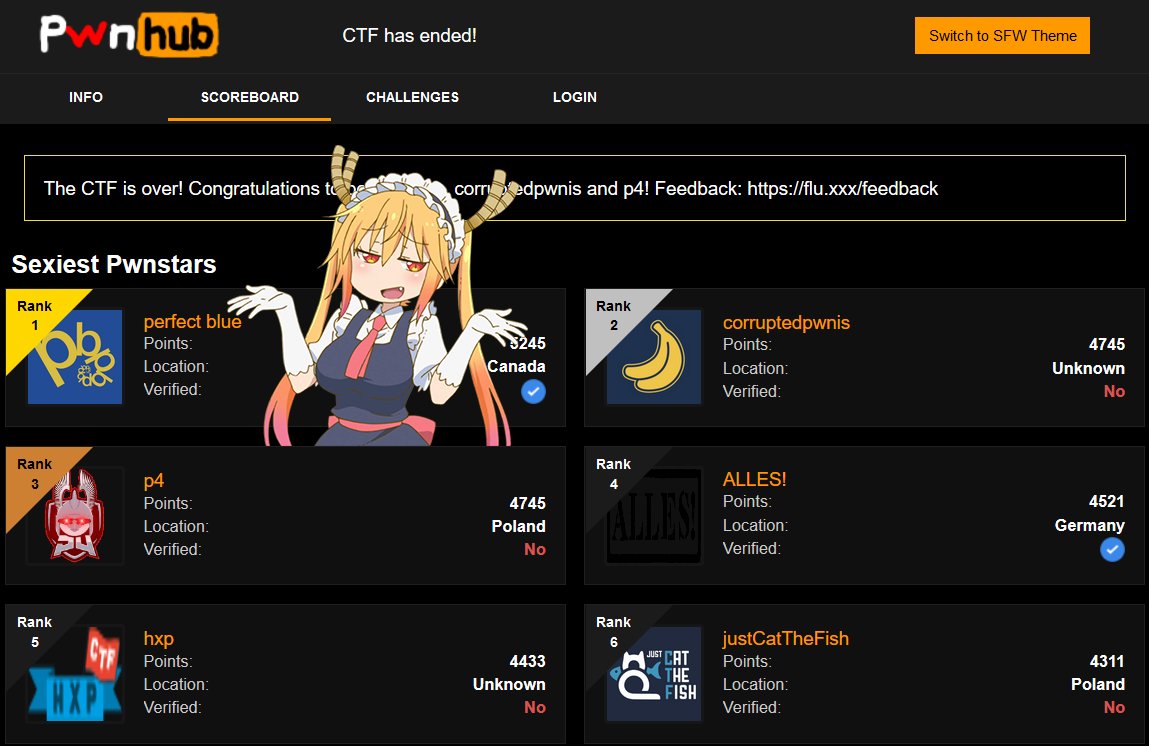
In November, we participated in the CSAW CTF Finals 🇺🇸. Organized by NYUSEC, it’s the most prominent undergraduate competition in the US. Because we met there, CSAW has always been an important annual team tradition (and also an excuse to party with other CTF players). Of course, this year’s CSAW was online-only. Returning to CSAW finals as the defending champions, we achieved a clean victory to defend our title.

The week after, we joined forces with our friends at Super Guesser to compete in Balsn CTF 🇹🇼, and we won. This was a great sign for our collab’s future.
The following week, we played with Super Guesser again in Dragon CTF 🇵🇱. Dragon Sector, the organizing team, is one of the best CTF teams in the world with 3 CTFTime seasons under their belt. They certainly didn’t let down our high expectations for the competition quality. The CTF had us on the edge of our seats with how close it was, especially at the end. After 48 hours of non-stop hacking, we emerged victorious.

Shoutout to ALLES! and hxp for those awesome moments. Not to mention the memes that came as a result as well [1] [2]. (Sorry DS 😛)
A week after that, we participated alongside Super Guesser in HITCON CTF 🇹🇼. HITCON is another world-class event with challenges ranging from hard to mind-bending with nothing in between. This CTF is organized by HITCON, a group of players from 217—a Taiwanese powerhouse. The quality and difficulty of this event were great as usual.
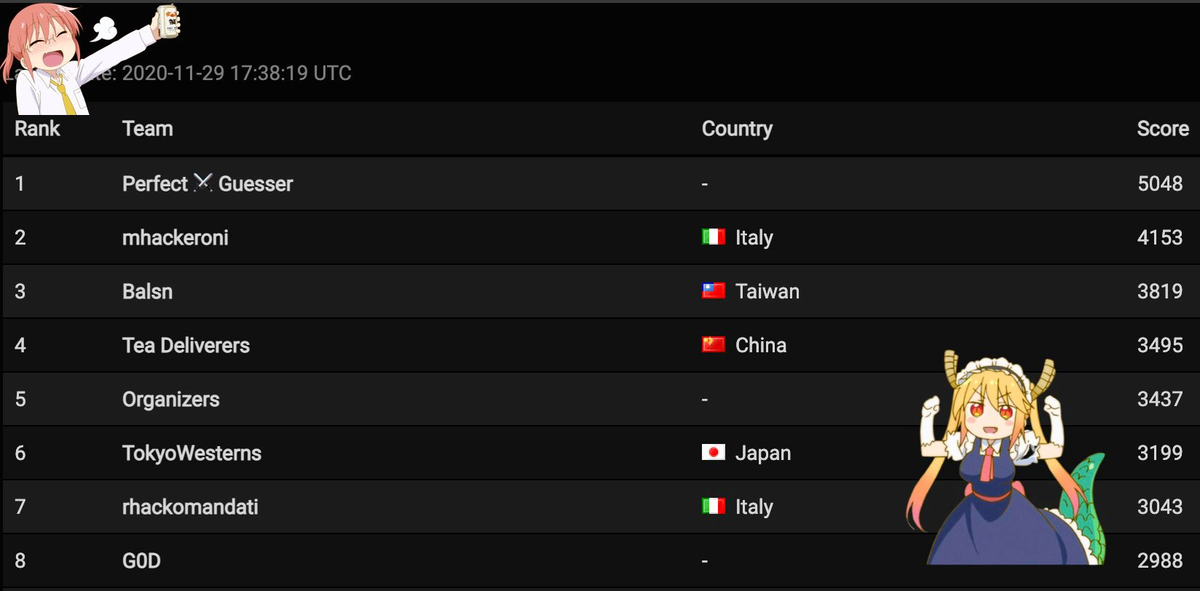
After 48 ruthless hours, we stood at the top of the scoreboard and won the event. This victory also directly pre-qualified us for DEF CON 2021 finals—a huge moment for our team, having finally achieved one of our long-time goals.
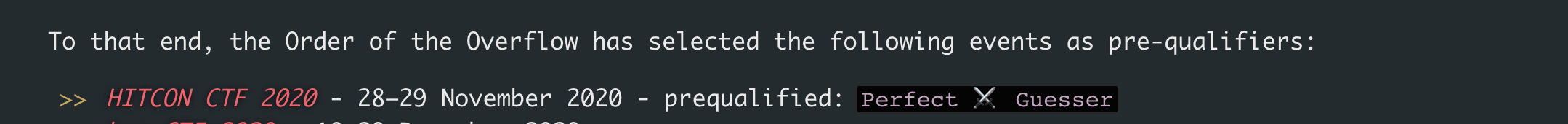
At the start of December, we hosted our own CTF, pbctf. We wanted to give back to the community and provide a great competition for everyone. We featured challenges from easy to punishingly difficult. Our goal was to create a CTF we’d personally love to play, and we were glad that other teams also agreed. Sitting on the other side of the table as the organizers taught us valuable lessons. Shoutout to sampriti for staying up all night fighting with Kubernetes and making sure the challenge infrastructure stayed online.

A week after that, we played in ASIS CTF Finals 🇮🇷 and won again.
For our final CTF this year, we played again with Super Guesser in hxp CTF. In the festive spirit, we played casually, attempting to dethrone pasten. Unfortunately, that remains a task the CTF community has yet to solve. In the end, we placed 3rd.
Wrap-up
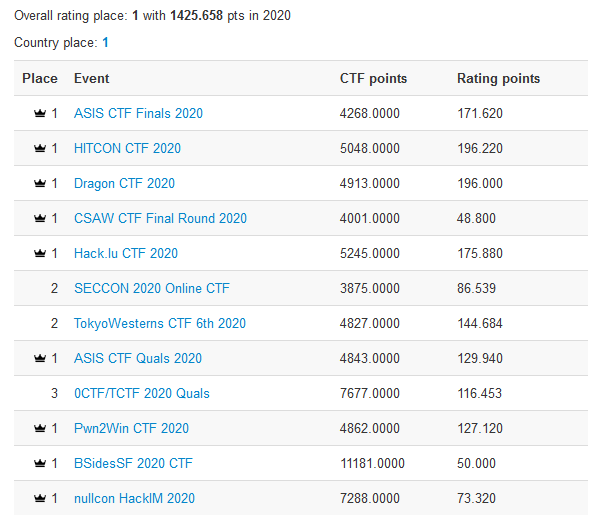
That pretty much concludes our 2020 CTF experience. We were glad to have performed so well, though it’s a bummer all the free trips were canceled. Here was our final CTFtime rating breakdown:
| Place | Event | Points |
|---|---|---|
| 1 | HITCON CTF 2020 | 196.2 |
| 1 | Dragon CTF 2020 | 196.0 |
| 1 | Hack.lu CTF 2020 | 175.9 |
| 1 | ASIS CTF Finals 2020 | 171.6 |
| 2 | TokyoWesterns CTF 6th 2020 | 144.6 |
| 1 | ASIS CTF Quals 2020 | 129.9 |
| 1 | Pwn2Win CTF 2020 | 127.1 |
| 3 | 0CTF/TCTF 2020 Quals | 116.4 |
| 2 | SECCON 2020 Online CTF | 86.5 |
| 6 | 0CTF/TCTF 2020 Finals | 81.2 |
| - | Total | 1425.7 |
And here’s also the overall CTFtime scoreboard. Congratulations to the other top teams, especially MSLC, hxp, TokyoWesterns, and PPP for their outstanding performance.
| Place | Team | Country | Rating |
|---|---|---|---|
| 1 | perfect blue | 🇺🇸 | 1425.658 |
| 2 | More Smoked Leet Chicken | 🇷🇺 | 1084.136 |
| 3 | hxp | 🌐 | 823.585 |
| 4 | TokyoWesterns | 🇯🇵 | 797.192 |
| 5 | Plaid Parliament of Pwning | 🇺🇸 | 786.941 |
| 6 | ALLES! | 🇩🇪 | 761.812 |
| 7 | Balsn | 🇹🇼 | 752.090 |
| 8 | p4 | 🇵🇱 | 727.637 |
| 9 | Tea Deliverers | 🇨🇳 | 675.999 |
| 10 | Dragon Sector | 🇵🇱 | 669.334 |
See you all next year!
Moving forward
• We plan to host pbctf again next year. 🚩 We had a great time organizing our own CTF, and we definitely plan to return next year. Look forward to it!
• Tips and tricks for CTF players. One of the key factors for success in CTF (and life in general) is just experience. We’re able to solve certain challenges really quickly because we’ve just straight-up seen them before. The first time you solve a Linux kernel pwn, QEMU pwn, Chromium pwn, etc. is obviously the hardest. But after that, it’s extremely common to just recycle past solutions and writeups. So one of the key strategies for us is to stockpile solution templates. For us at least, there’s no excuse for not having a canned solution when encountering a stereotyped problem. From our experience, we would say around 50% of challenges are stereotyped.
Another aspect of experience is know-how: the little tricks and tactics that you learn over a long time. These are things like knowing all the arcane ins-and-outs of your tools and having a good intuition for how a task can be solved. One could say that the most valuable educational aspect of CTFs is that they force you to develop this kind of practical experience. Necessity is the mother of invention—we’ve learned a lot of tools in-depth as a result. Of course, at the top level there’s also plenty of expedient tactics that save time and win competitions, like low-latency brute and so on.
These two points aren’t unrealistic. Far from a departure from real-world security, looking at past vulnerabilities and write-ups in “real life”, you’ll notice the same trends. First, the security community focuses on the same few “big targets” each year, like browsers, hypervisors, kernels, etc. It’s not at all surprising that the researchers and professionals who work with these targets every day make challenges based on what’s familar to them. Second, knowing how to use your tools properly is pretty much essential in security. The importance of tooling is universal: it could mean the difference between 1 month of manual effort or just 1 hour. That’s one thing we love about CTFs: they’re very practical and the skills and knowledge easily transfer.
• As professional CTF players (and as humans), we are prone to burnout: The grass is not always greener on the other side. The CTF scene in 2020 is not the same as it was back in, say 2016. The number of CTFs is always growing. To put that in perspective, there were ~90 total events in 2016 and ~200 in 2020, a 100% growth rate in last 4 year. Similarly, the number of top-tier events are also increasing steadily. This shows that CTFs are getting famous. Staying at the top of the game requires maximizing winning in such mega-events. Winning these top CTFs is not easy (as you have just read), and it’s an intellectually taxing and often stressful activity.
Being a top performer requires sacrifice. Most of our team members are full-time professionals or students. Thus, it’s challenging to balance work, personal lives (yes, we do have them), and CTF. To avoid any bad circumstances that could arise in the future, moving forward we plan to schedule well in advance which events to full tryhard. We want to maintain our tight-knit team culture. In the end, we are good friends before anything else.
Conclusion
We had a blast playing CTFs this year, despite the quarantine. We made a lot of new friends, rose to the challenge, and outperformed our expectations. We’re looking forward to next year!
If you’d like to keep up with any new developments from our team, you can follow us on Twitter.
Appendix: What are CTFs?
CTFs, or Capture The Flag, are technical competitions designed for students and professionals which teach concepts relating to information security. CTFs require participants to solve challenges mimicing real-world security flaws and sharpens skills through hands-on experience. You can read more about CTF here.
CTFTime is a platform which tracks CTF team ratings, statistics etc. You can think of it as like an informal global leaderboard. You can find more on their About page.

